is the rfid chip true or false RFID tags can replace bar codes and QR codes. A bar code can only be read if the reader can visually see the bar code. RFID tags can be read if the reader is nearby, even if a bar code . See more 24 votes, 45 comments. trueThe NFC-enabled device, in this case, the Samsung Galaxy S4, acts as the .
0 · what is rfid technology
1 · what is rfid security
2 · what is rfid card
3 · what is a rfid system
4 · types of rfid
5 · rfid vs barcode
6 · rfid unique identity
7 · are rfid tags safe
The ACR122U-SAM is connected to a computer through USB as specified in the USB .
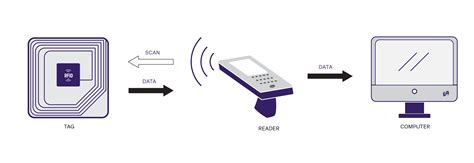
RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID . See moreSome people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with contactless payment information embedded in them. Identity thieves could read the same information from an RFID . See moreRFID tags can replace bar codes and QR codes. A bar code can only be read if the reader can visually see the bar code. RFID tags can be read if the reader is nearby, even if a bar code . See more
Not every successful reading of a tag (an observation) is useful for business purposes. A large amount of data may be generated that is not useful for managing inventory or other applications. For example, a customer moving a product from one shelf to another, or a pallet load of articles that passes several readers while being moved in a warehouse, are events that do not produce da. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a .Although many wallets and passport holders are advertised to protect personal information, there is little evidence that RFID skimming is a serious threat; data encryption and use of EMV chips rather than RFID makes this sort of theft rare.RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person.
Put simply, RFID is similar to barcode technology but uses radio waves to capture data from tags, rather than optically scanning the barcodes on a label. RFID does not require the tag or label to be seen to read its stored data—that's one of the key characteristics of an RFID system.
what is rfid technology
Myth #1: RFID Is Only for Big Organizations. RFID technology provides the most efficient and accurate way for organizations to track, trace, and monitor assets, and enterprises of all sizes can benefit from the improved asset visibility and management facilitated by RFID. Anti-shoplifting alarms use a technology called RF (radio-frequency), while a similar (but more advanced) technology called RFID (radio-frequency identification) has many other uses, from tracking pets and public library stocktaking to collecting fares from bus passengers. RFID chips are easily cloned or copied: There is a misconception that RFID chips can be easily cloned or copied, leading to concerns about identity theft and fraud. While there have been instances of RFID chip cloning, it requires significant expertise and .Radio frequency identification (RFID) describes a system that uses radio waves to identify an object or person. There are three key components to an RFID system: •Tag: •Reader: •Database: A radio antenna attached to a microchip which stores a .
A RFID chip is another term used to define a RFID tag. It is a tag, label or card that can exchange data with a reader using radio frequency (RF) signals. It usually has a built-in antenna and an integrated circuit IC).
what is rfid security
Radio frequency identification (RFID) is a generic term that is used to describe a system that transmits the identity (in the form of a unique serial number) of an object or person wirelessly, using radio waves. It’s grouped under the broad category of . A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a .
Although many wallets and passport holders are advertised to protect personal information, there is little evidence that RFID skimming is a serious threat; data encryption and use of EMV chips rather than RFID makes this sort of theft rare.
RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person.Put simply, RFID is similar to barcode technology but uses radio waves to capture data from tags, rather than optically scanning the barcodes on a label. RFID does not require the tag or label to be seen to read its stored data—that's one of the key characteristics of an RFID system.
Myth #1: RFID Is Only for Big Organizations. RFID technology provides the most efficient and accurate way for organizations to track, trace, and monitor assets, and enterprises of all sizes can benefit from the improved asset visibility and management facilitated by RFID. Anti-shoplifting alarms use a technology called RF (radio-frequency), while a similar (but more advanced) technology called RFID (radio-frequency identification) has many other uses, from tracking pets and public library stocktaking to collecting fares from bus passengers. RFID chips are easily cloned or copied: There is a misconception that RFID chips can be easily cloned or copied, leading to concerns about identity theft and fraud. While there have been instances of RFID chip cloning, it requires significant expertise and .
2021 afc north standings
Radio frequency identification (RFID) describes a system that uses radio waves to identify an object or person. There are three key components to an RFID system: •Tag: •Reader: •Database: A radio antenna attached to a microchip which stores a . A RFID chip is another term used to define a RFID tag. It is a tag, label or card that can exchange data with a reader using radio frequency (RF) signals. It usually has a built-in antenna and an integrated circuit IC).
cardinals standings football

what is rfid card
NFC can be used to read tags and for Apple Pay. To use, make sure your iPhone is unlocked, and then tap the top of your iPhone's back on the tag to get a pop-up. Unfortunately, .
is the rfid chip true or false|types of rfid